Api Key In Url Security
API key security is an excellent option for authentication but a less-than-ideal option for authorization meaning that simple read-only APIs which require less granular permissions may function better. Anybody can easily identify the API key and make requests to your server.
Again in case of HTTP network traffic can be sniffed and API key can be stolen.
Api key in url security. To register a user send a POST HTTP request to this endpoint httplocalhost8000apiregister and input the appropriate details as shown here. To help you use API keys as effectively as possible lets walk through some common pitfalls we see come up and learn how to handle sensitive data in Postman. Then permissions are changed so that only the user can read the file.
You must have at least one API key associated with your project. The API key is a unique identifier that authenticates requests associated with your project for usage and billing purposes. API keys are supposed to be a secret that only the client and server know.
The popular method for early APIs its certainly easy to pass an API key through a query string in a URL. Likewise for security reasons and future-proofing we recommend that you use that same order when choosing a method for sending the API Key. API keys that are embedded in code can be accidentally exposed to the public for example if you.
For example create separate API keys for your Android app and. If you want to join along in Postman with more detailed explanations import the full tutorial here and follow the step-by-step documentation. To keep your API keys secure follow these best practices.
A REST API over the web cannot be secured unless you ask the user to login with his credentials. When it comes to read-only data theres almost nothing as secure as an API key. API key is some random hash which uniquely identifies the consumer.
Reading post so far turned out there is not a single API authentication protocol that is secure if not. When the keysecret pair is downloaded it is saved to the local file system. The url gets stored in access logs on the server side.
Admin keys convey write permissions on the service and also grant rights to query system information. This is typically done using a hash-based message authentication code HMAC. An essential part of API security is the use of API keys.
Publicly exposing your credentials can. When you use API keys in your applications ensure that they are kept secure during both storage and transmission. Do not embed API keys directly in code.
API keys have numerous benefits over usernamepassword mechanism. In other words favour the use of HTTP Basic Authentication over the URL query string and try to avoid the body field. The session token or API key should be sent along as a cookie or body parameter to ensure that privileged collections or actions are properly protected from unauthorized use.
No Keys in the Channel. This Key is typically a long string of generated characters which follow a set of generation rules specified by the authority that creates them. API keys are generated when the service created.
Api keys are tokens that can be used to make REST API calls without needing to provide user credentials along with the request. Im going to reference the Postman tutorial called Securely Using API Keys. In response to segfaults comments - A website user generally does not enter an API key.
However this method can risk API key exposure since despite encryption the parameters can be stored in web server logs. Storing Your API Security Key At Stormpath we encourage storing the API keysecret in a file only readable by the owner. Now your details might not be similar to this but here is what the key and value of your requests should look like.
Public web service operators can use API keys to rate-limit API calls and reduce denial of service attacks. Instead of adding the plaintext API key to a request we will use the API key to sign each request. Like Basic authentication API key-based authentication is only considered secure if used together with.
An API Key is a piece of code assigned to a specific program developer or user that is used whenever that entity makes a call to an API. Usernames passwords session tokens and API keys should not appear in the URL as this can be captured in web server logs which makes them easily exploitable. API keys are used to control access to public REST services.
When using an api key to access a resource in Maximo no user session is created in Maximo so that user sessions do not need to be maintained no logout is required. Okay lets look at three ways to securely work with API keys. So never use this form of security.
There are two kinds of keys. One way to improve security is to keep the API key out of the channel. API keys have become the standard when consuming an API.
Protect against cross-site request forgery. Passing a valid API key on the request is considered proof that the request is from an authorized client. Use a separate API key per source and restrict each with an application restriction.
For paid API services API keys also allow you to provide access based on the access plan purchased. The above URL exposes the API key.
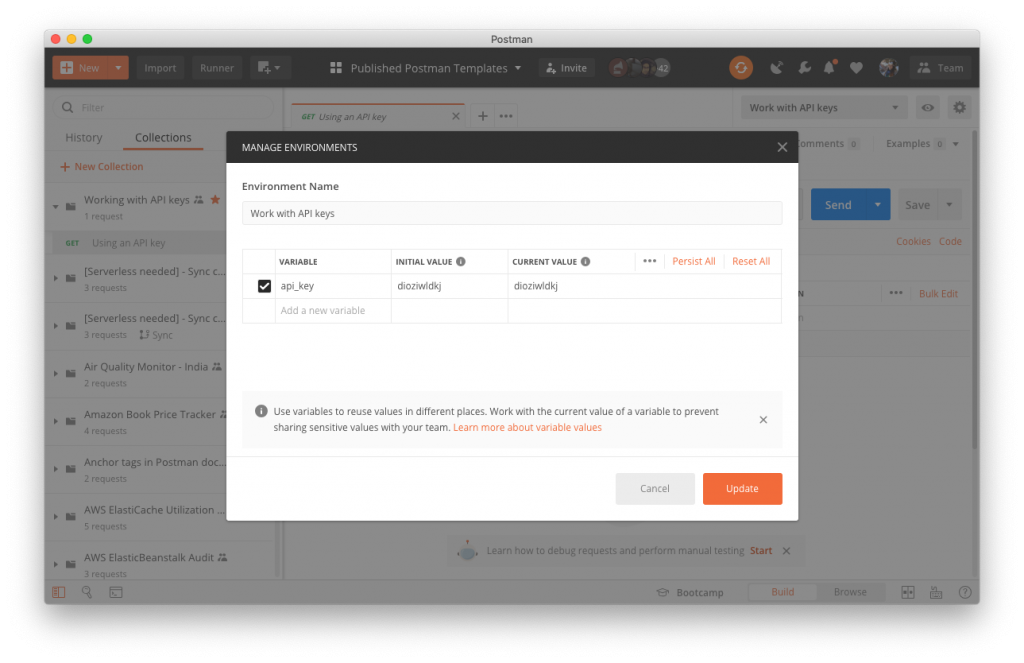
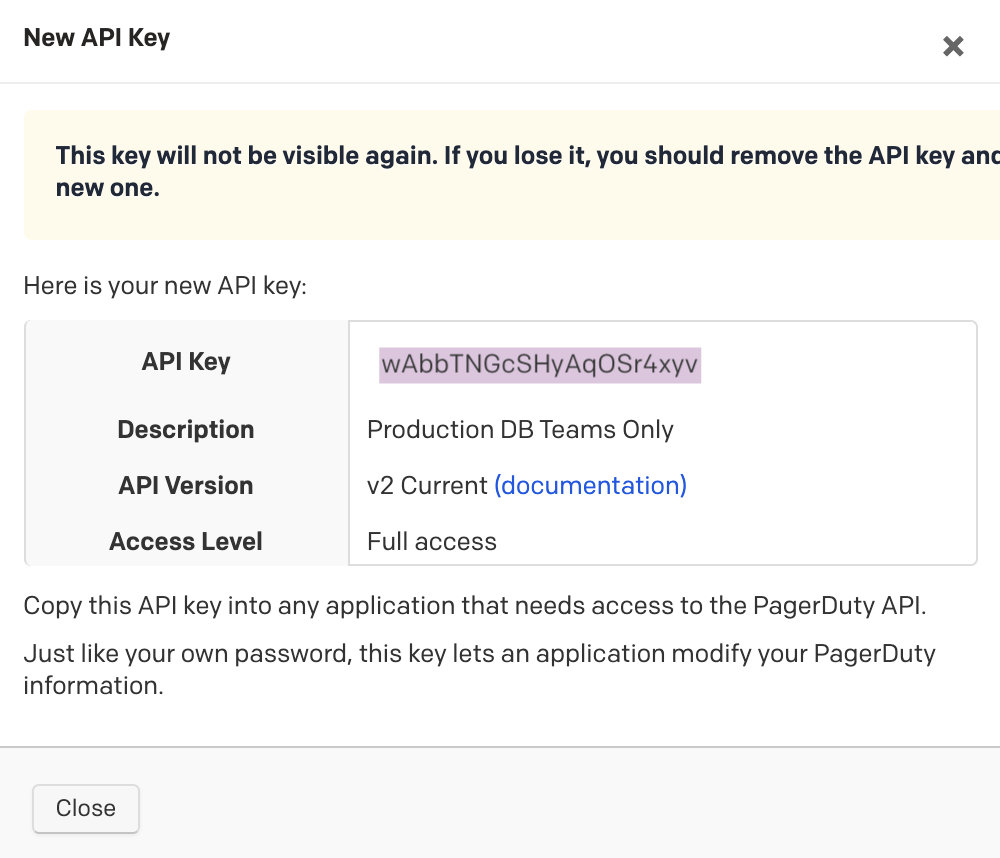
How To Use Api Keys In Postman Postman Blog
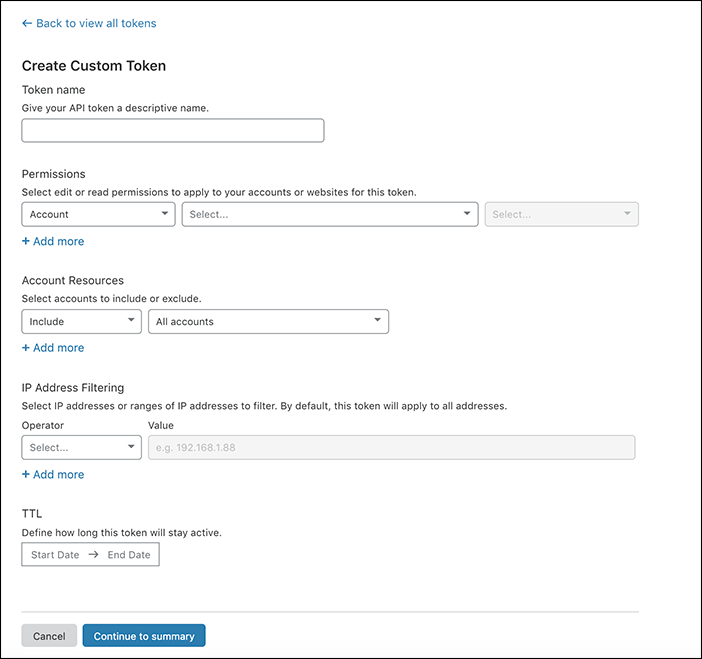
Managing Api Tokens And Keys Cloudflare Help Center

How 3scale Supports Oauth V1 And V2 3scale Api Management Platform Development Supportive Red Hats

Api Keys Kibana Guide Master Elastic

Iphone Development Integrate Gyft Api In Ios Integrity Current Time Api Key
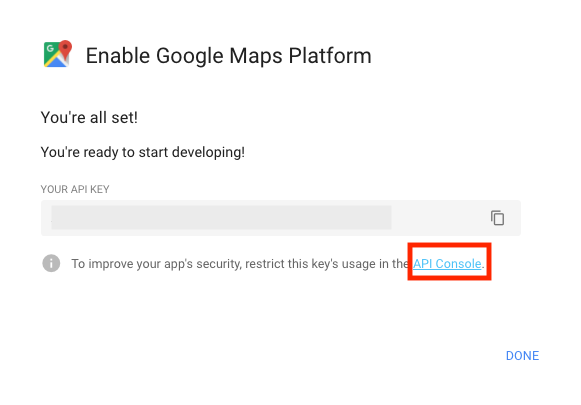
Creating A Google Maps Api Key Wp Google Maps
Api Keys Kibana Guide Master Elastic

Envkey Wants To Create A Smarter Place To Store Api Keys And Company Identification Information Api Key Key Key Storage
Api Key Authentication Azure Cognitive Search Microsoft Docs

Gitroller A Git Recon Tools Git Computer Security Tools

How To Embed Bing Maps In Wordpress Check More At Https Www Latestblog Org How To Embed Bing Maps In Wordpress Bing Maps Wordpress Blog Post Basic Website
How To Generate And Set A Google Maps Api Key Yoast
How To Use Api Keys In Postman Postman Blog
How To Use Api Keys In Postman Postman Blog




Post a Comment for "Api Key In Url Security"