Api Key Length Best Practice
Some systems have a way to issue API keys on demand. John Au-Yeung and Ryan Donovan.
Key scoping - Use separate keys for production development and testing environments.
Api key length best practice. They can also be used together. Now if we were to take that same example but change the length of our hash from 3 to 5 we would get an N that is much larger exponentials are good like that. Data is essentially the currency with which companies attract users and conduct business.
API Key Best Practices and Examples. Check out these five best practices for safe API key storage and avoid the headaches of an exposed key. The restriction becomes part of the API key definition after this step.
We can save the request token and secret in session for later exchange. The best rule of thumb I can give is to not transmit any secret directly because of the man-in. An example of such an API key is zaCELgL0imfnc8mVLWwsAawjYr4Rx-Af50DDqtlx.
Embedding your API key in your source code may seem like a practical idea but its a security risk as your source code can end up on many screens. API keys that are generated must also use Alphanumeric and special characters. Best practices for REST API design.
For example if youre creating a user account with the Okta API youll need to include your API key in that request for it to succeed. The API requests include the API key usually in a request header. Dont store your API key directly in your code.
Select the API key that you want to set a restriction on. Hash_hmac string algo string data string key echo hash_hmacsha1 Message Secret Key. Organize the API around resources Focus on the business entities that the web API exposes.
Go to the Credentials page. Basic API Key Security. 850 PM Best practices for securely using API keys Cloud Securely API keys Monitoring APIs Setting up API keys Edit When you use API keys in your applications take care to keep them secure do the following Steps -.
GET HTTP11 Host. So securing APIs is critical. Next we need to get the access tokens.
In this article well look at how to design REST APIs to be easy to understand for anyone consuming them future-proof and secure and fast since they serve data to clients that may be confidential. The total URI including the Path and the Query MUST NOT exceed 2000 characters in length including any formatting codes such as commas underscores question marks hyphens plus or slashes. Go to the Google Maps Platform Credentials page.
The API key property page appears. API keys behave similarly to passwords in the Gateway. So for that use case you should use a hash of more than 3 characters in length.
Since the API key itself is an identity by which to identify the application or the user it needs to be unique random and non-guessable. This is important to prevent all of the same problems coming up again with your internal API. API Security Best Practices.
N 62⁵ 900000000. API security is one of the biggest concerns for any business using APIs to deliver data. Earlier we suggested Basic Auth as an alternative to API keys.
Level 3 corresponds to a truly RESTful API according to Fieldings definition. Most implementations pair the API key with a blank value for the unused field username or password. To restrict an API key.
The web API stores information about the request in a table held in table storage or Microsoft Azure Cache and generates a unique key for this entry possibly in the form of a GUID. B8e7ae12510bdfb1812e463a7f086122cf37e4f7 o new oAuthMY_CONSUMER_KEY. Here are the API security best practices.
We strongly recommend that you follow the instructions to set restrictions for your API keys. API keys that are embedded in code can be accidentally exposed to the public for example if you forget to remove the keys from code that you share. To keep your API keys secure follow these best practices.
They are used to login to an associated account that allows transaction and account actions many just like with a username and password combination. The Restrict and rename API key page appears. Just like passwords API keys should be rotated to prevent a compromised key from being abused.
If you have different applications modules or programs that use the same APIs then separate those keys too. REST APIs are one of the most common kinds of web services available today. Click the Select APIs drop-down and select the APIs or SDKs you want your application to access using the API key.
Im not asking for a specific language just the general approach to creating keys should they be an encryption of details of the users app or a. All the keys vary in length and the characters they contain Im wondering what the best approach is for generating an API key. This article provides some best practice guidance for managing API keys and accounts they are tied with.
Instead of embedding your API keys in your applications store them in environment variables or in files outside of your applications source tree. The web API initiates the processing as a separate task. Do not embed API keys directly in code.
Key used for generating the HMAC. The web API records the state of the task in the table as Running. Instead store your API key and secret directly in your environment variables.
API Key Generation. When youre using a REST API especially one that incurs costs or has usage limits you need to use an API key to access the API in question. Protecting Keys Securing your API keys properly will reduce the likelihood of your credentials being hijacked.
These keys may only be valid for hours or minutes limiting the exposure of a compromised key. If an API or SDK is not listed you need to enable it Click Save. For more information see API security best practices.
You can pass the API key via Basic Auth as either the username or password. The following best practices will help ensure you have a reliable and secure integration with any external API. In practice many published web APIs fall somewhere around level 2.
You then have to decide how best to communicate with your servers to ensure they are protected.

This Tutorial Explains How To Use Flatlist Component In React Native Applicationand Apply Set Onpress Event Onflatlistto G React Native Components How To Apply

Beginner React 2019 Create A Movie Web App Basic Coding Web App App Course

Pro Cat Eyeliner Eye Shadow Stencils 2pcs Set With Images Eyeliner Stencil Cat Eyeliner Stencil

Https Sapabapcentral Blogspot Com 2020 07 Sap Abap Programming Model For Fiori List Report Application Part 3 Html Sap List Application

Ad Fs Certificates Best Practices Part 2 Key Size The Things That Are Better Left Unspoken

Content Writing Vs Copywriting Difference Copywriting Content Writing Copywriting Infographic

Autodesk Artcam 2018 X64 64bit Product Key And Xforce Keygen In 2021 Autodesk Solutions The Fault In Our Stars

How Do I Add The Star Wars Intro To My Ios And Android Mobile Apps Intro Star Wars Mobile App

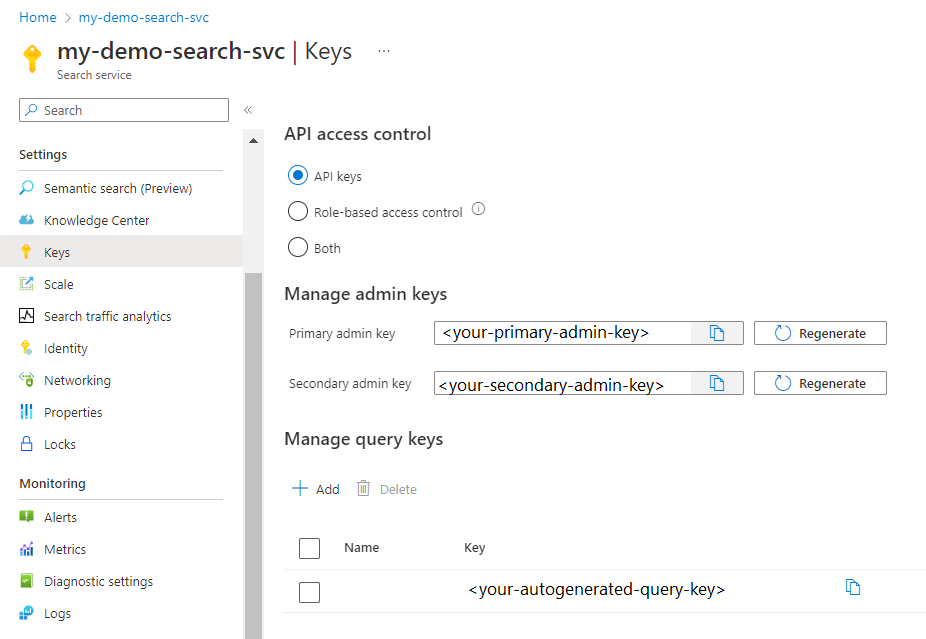
Api Key Authentication Azure Cognitive Search Microsoft Docs

Mitosis Meiosis I Meiosis Ii Comparison Anchor By Iteachbio Teachers Pay Teachers Mitosis Mitosis Meiosis Meiosis
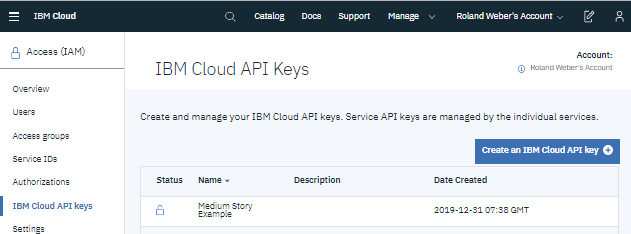
Api Keys What S The Point When And Why To Authenticate With Api By Roland Weber The Startup Medium

Hole Jeans Cat Printing Shorts Men Five Point Jeans Casual Knee Length Short Knee Length Shorts Mens Outfits Clothes Design

Cryptocurrency Trading Bots Ultimate Guide September 2019 Cryptocurrency Trading Best Crypto Technical Trading

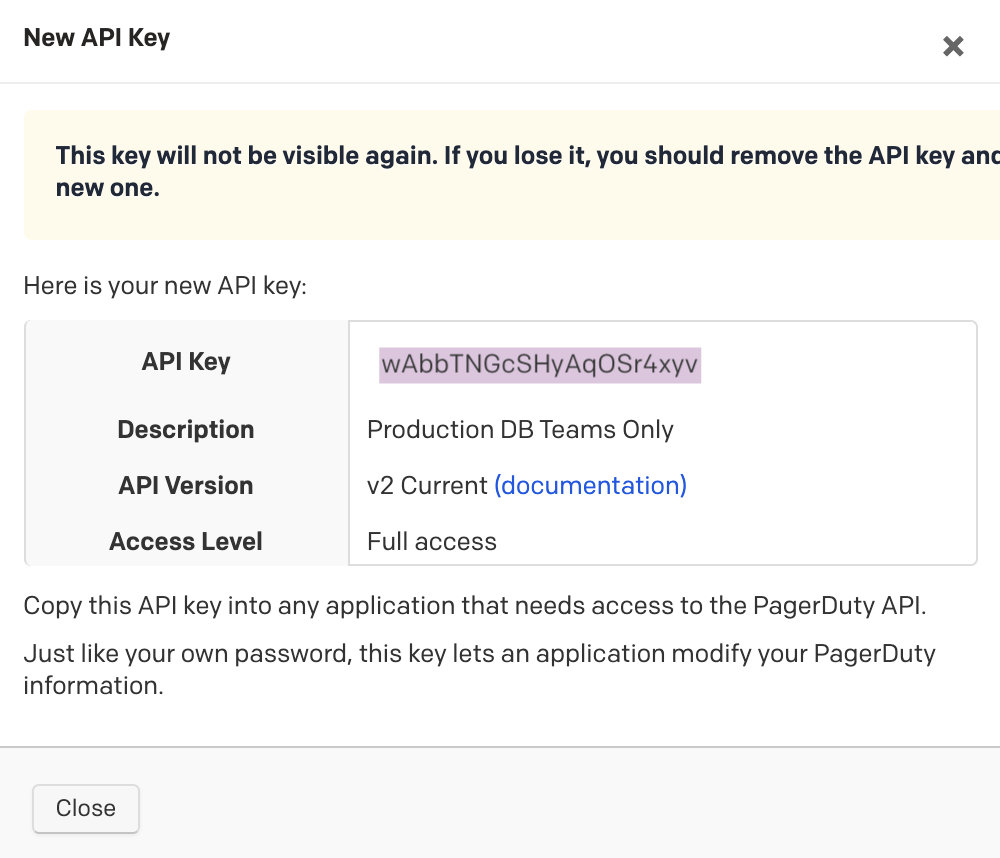

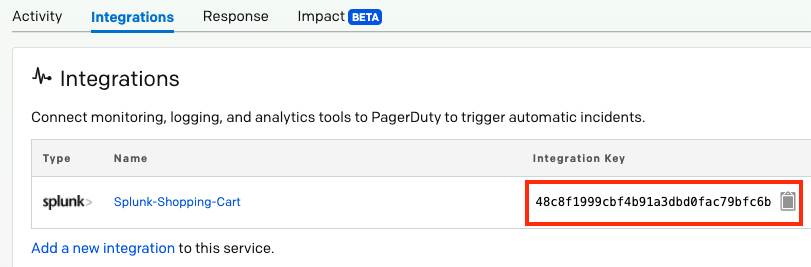
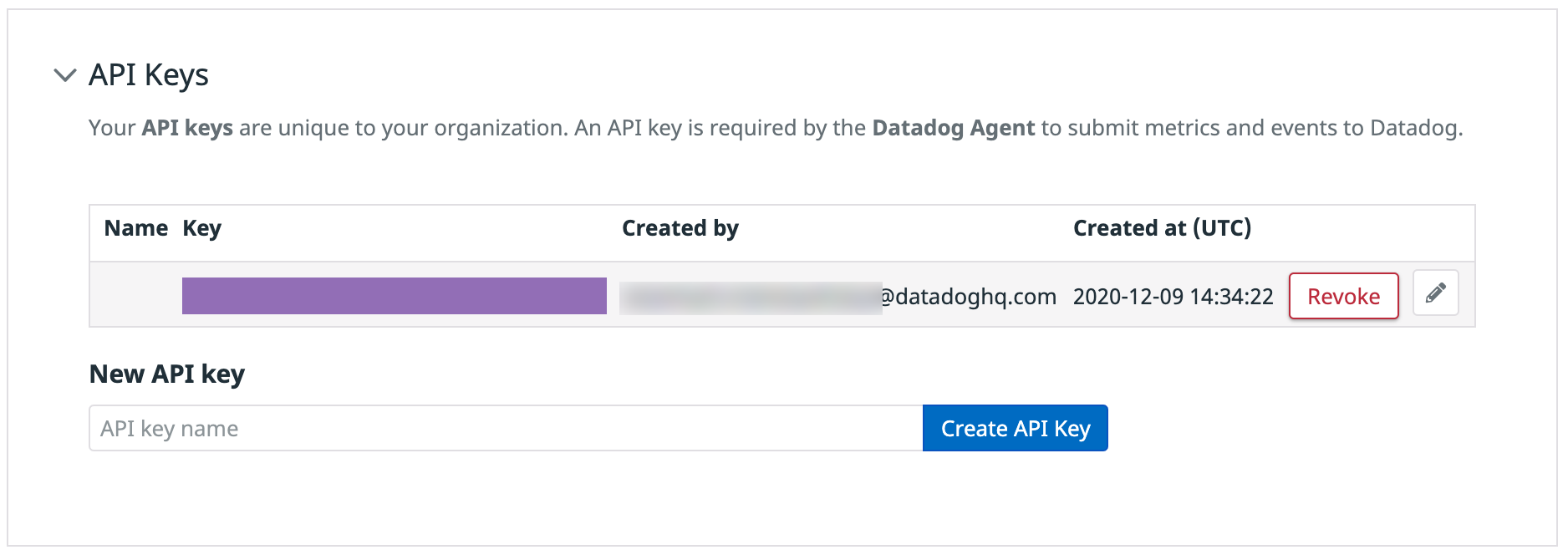
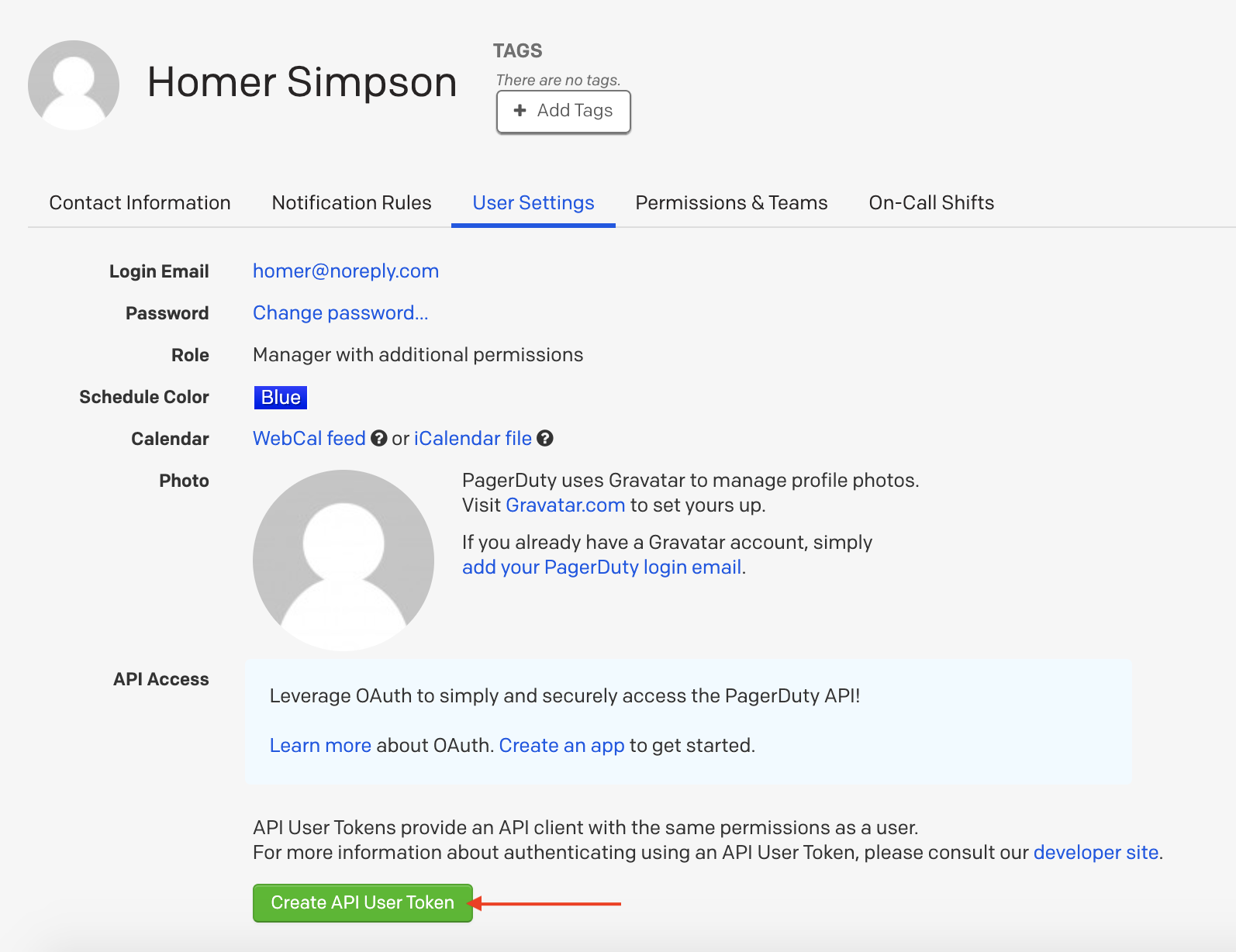
Post a Comment for "Api Key Length Best Practice"